Conducting a Vulnerability Scan On a Small Business Environment

We will sign into our Greenbone Security Assistant to scan our environment. After conducting a scan we will document our findings so that we can mitigate any Security events.

Creating a Target
Before we create a target we will create a "New Credential" to group our data.
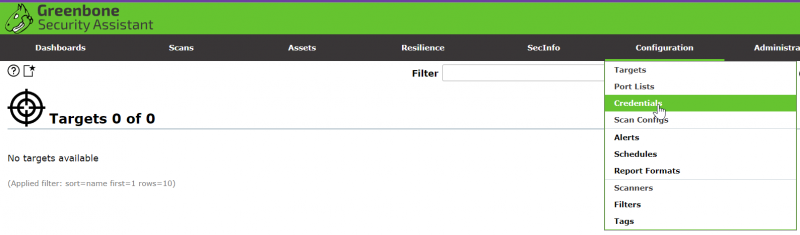
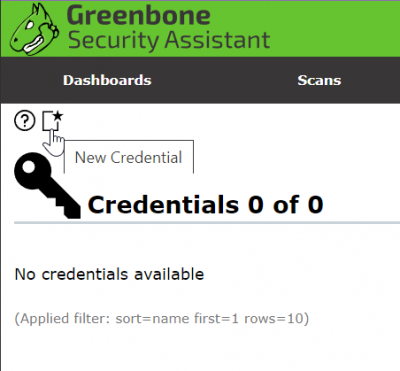
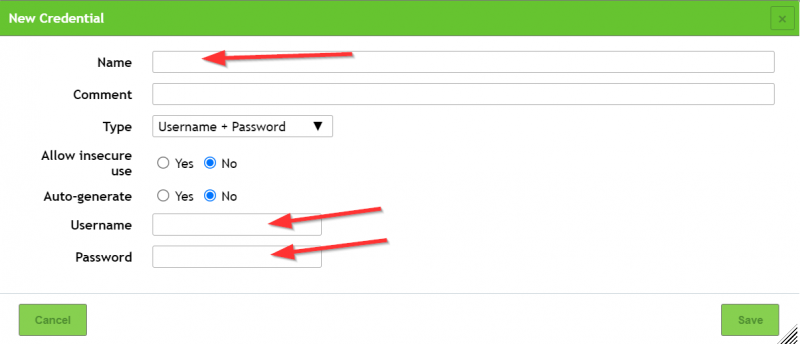
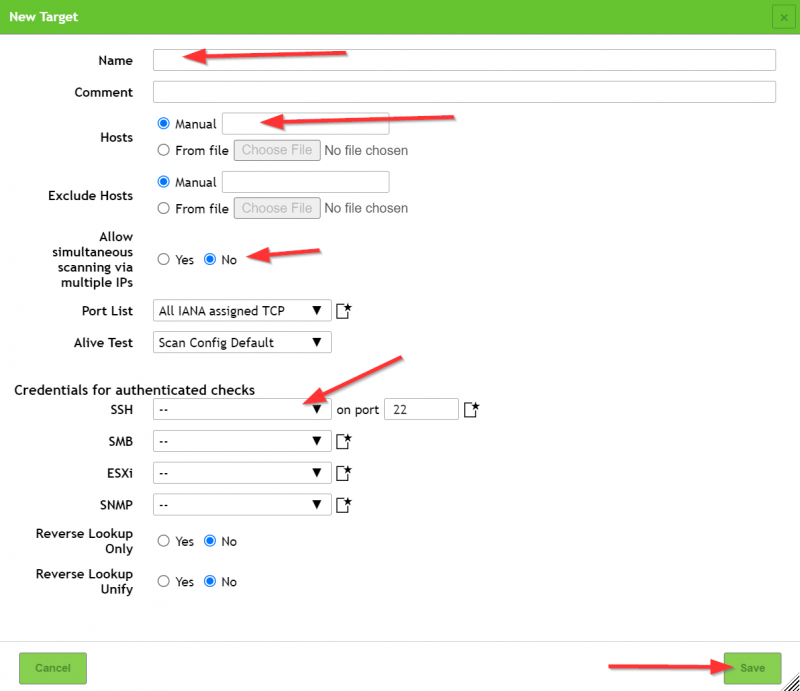
Next we will create the target to be scanned.
For the Host enter the wan-ip. You can find this in the fortigate console.
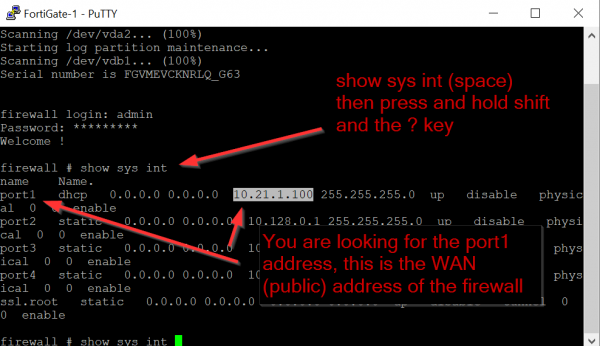
For SSH enter the credentials you have just created.
Last step before the scan, we will create a "Task Record"
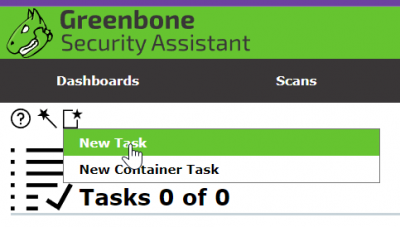
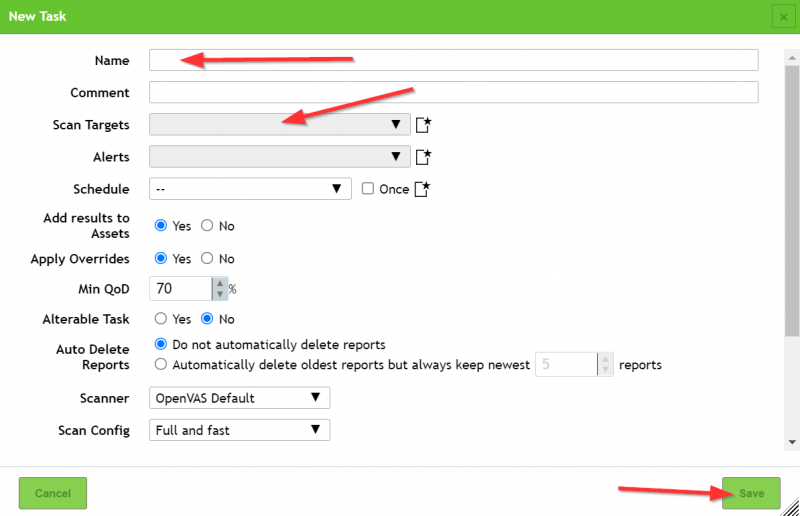
Scanning The Target
Once eall the profiles have been created go ahead and start the scan by clicking the play button.
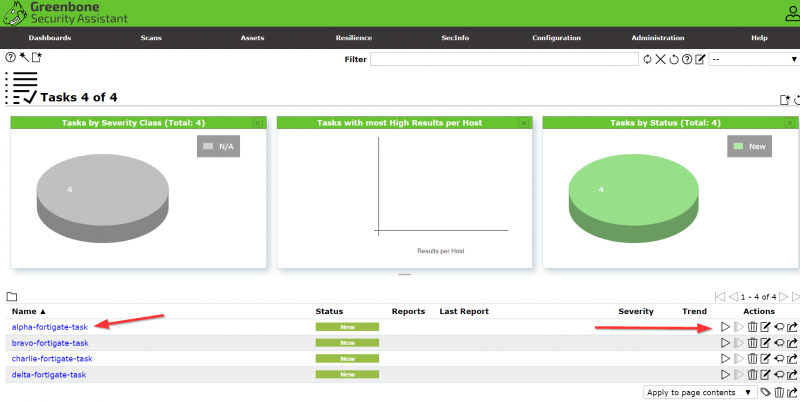
The scan may take up to an hour. Once the scan has finished downloading click the date to view the networks Vulnerability reports.
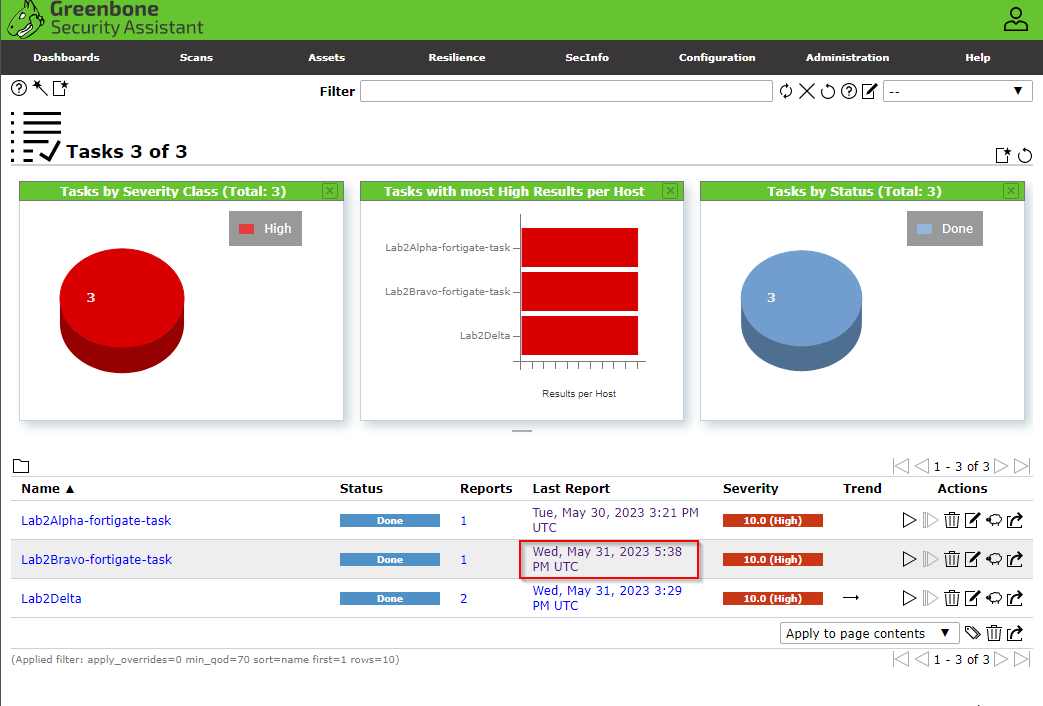
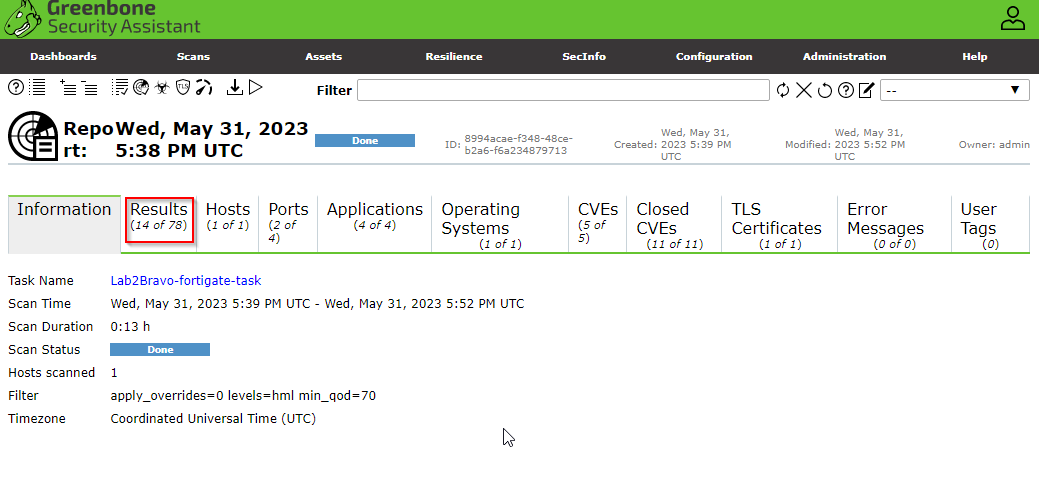
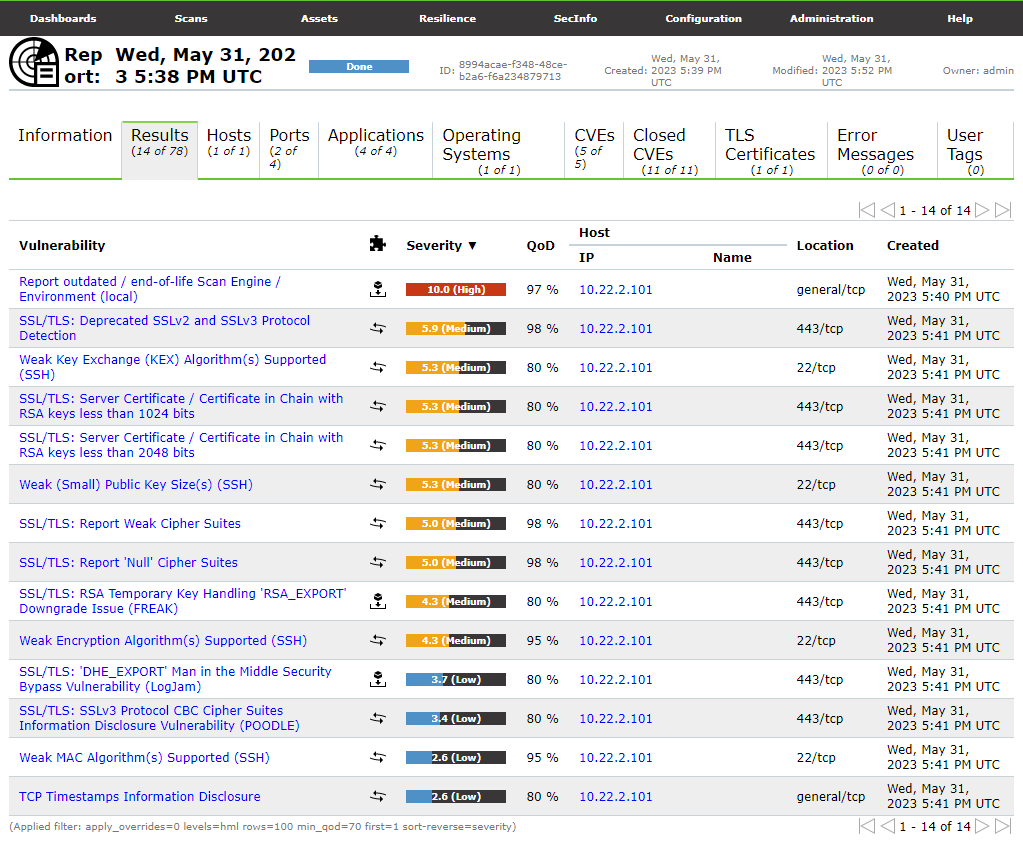
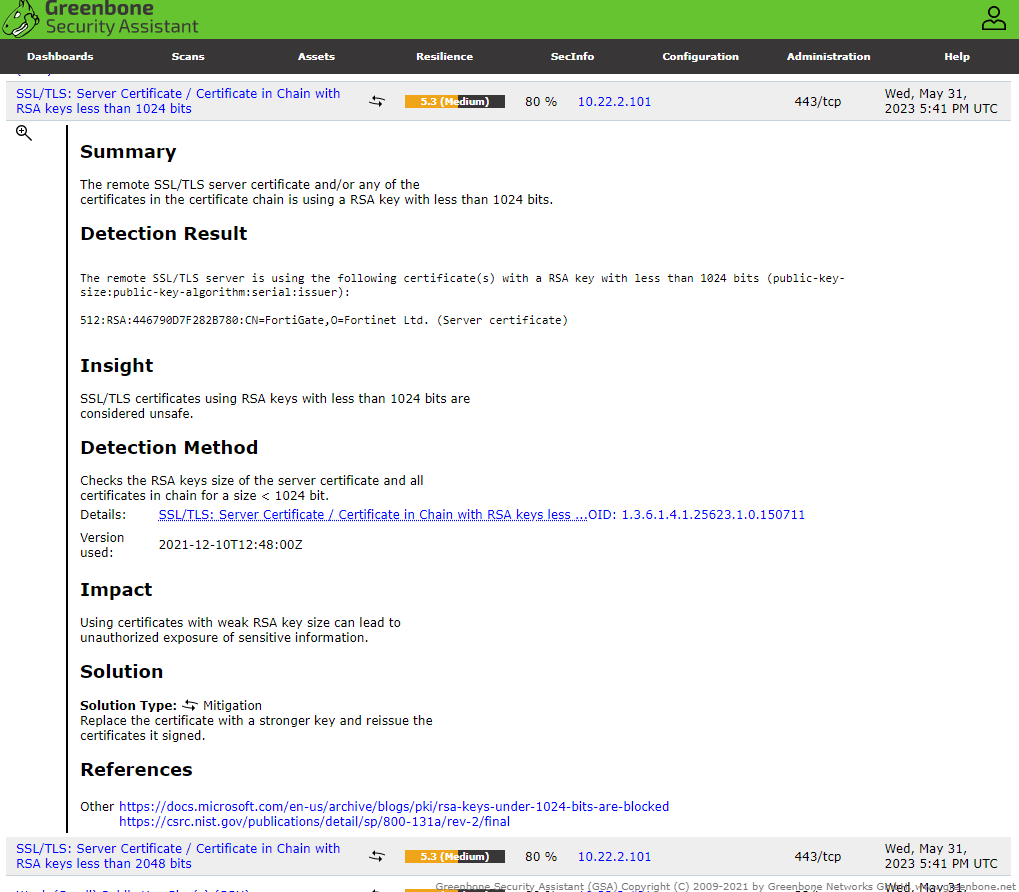
As you can see our business environment contains 13 major vulnerabilities. The page shows 14 because our first Vulnerability is that our Greenbone Assistant is outdated (we are using a trial version). You can inspect each vulnerability. They show a name, summary, detection result, insight, impact, severity, a solution, and other refreneces. This is a quick and easy way to anaylze an environment to make neccesary patches. You can also prepare for attacks, create risk assessments, and many more to ensure that the network is secured.
The last step would be to document all of the scans findings in a report and send it up to your Senior Engineer.